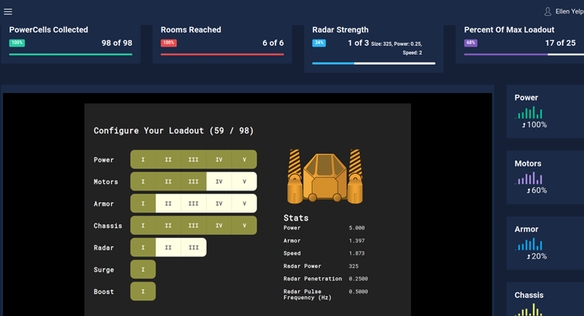
SANS Cyber Ranges focus on the practical application and assessment of hands-on cybersecurity training. The cyber range enables you and your team to apply skills you’ve learned in a curated and isolated environment, that gives you insight into what you are excelling at, and what you need to focus more on. You walk away with real world experiences on how to handle situations, without the real-world risk associated with practicing on live production equipment and systems. Then when you are back in the office you are prepared for whatever threats come your way. And as new threats and exploits come up, you can trust SANS to provide you with the latest information, research and strategies to deal with them all.
- Competitive and gamified
- For individuals and teams
- Practice and assess skills
- Isolated environments
- Capture-the-flag ranges & real-world simulations
- Expert tactics, hints, and tips
- Reduced response times
- Cyber Ranges for all skill levels
- Always up to date and cutting edge
New NetWars Core Version 9!
NetWars Core Tournament version 9 will take you deep into the upside-down cybersecurity world where all your hands-on cyber skills will be put to the test. More immersive than ever before, our gamified version 9 brings you all new real-world challenges, including Azure command line, Azure cloud penetration testing, cyber threat intelligence, and network protocol analysis.
Our 100% browser based NetWars challenge allows teams and individuals to play in this high-end interface platform.
NetWars Core Tournaments are only available at select, in-person SANS training events.
Storyline
Help a young group of friends in peril to find out who is behind a terrible danger, possibly involving the Hackins National Laboratory.
NetWars Continuous
Experience NetWars pressure-free with NetWars Continuous, a 4-month subscription to extended content.
- NetWars Ranges Available: Core and DFIR.
- Extended Engagement: Explore the intricacies of a subject matter thoroughly and be ready to apply learned skills effectively.
- Flexible Access: Crucial for individuals who need to balance training with other commitments and reduce travel costs.
- At Your Own Pace: Available 24/7, be ready to enable in-depth learning, practice, and assessment online anytime and anywhere.
NetWars is our premier Cyber Range, appropriate for all cybersecurity skill levels. NetWars poses a series of multifaceted, interactive and situational cybersecurity challenges. The challenges test a wide variety of disciplines and subject matter across 5 levels that increase in difficulty. These challenges may be completed individually or as a team. NetWars also features an automated hint system to help participants solve questions they may find particularly difficult. The available hints help participants develop new skills and ensure that every participant steadily progresses through the challenge.
- For individuals and teams up to 5, of all skill levels
- Custom virtual machine based challenges
- Scorecard of you or your teams performance upon completion
- Automated hint system; hints do not affect scores
- Real time score board of players/teams
All NetWars contains 5 levels, progressively increasing in difficulty, for players to advance through as they achieve and master new skill sets. This structure allows all participants, from beginners to experts, to find a fit for themselves in our ranges.
Level 1
For people new to information security (infosec) who are building their skills from the ground up.
Level 2
For entry-level infosec professionals with solid capabilities, who are beginning to build skills in specialized areas.
Level 3
For mid-level infosec pros with years of industry experience already under their belts, who are above average in skills and disciplines.
Level 4
For senior-level infosec pros who have developed specialized skills in cyber and are leaders not only at their organizations but also in the industry at large.
Level 5
For the elite-level infosec pros, capable of tackling the most advanced scenarios and challenges.
NetWars Formats
Tournaments vs. Continuous
| NetWars Tournament | NetWars Continuous | |
|---|---|---|
✓ | FUN COMPETITION - MOST CORRECT ANSWERS IN ALLOTTED TIME | |
✓ | MORE IN-DEPTH LEARNING ENVIRONMENT AND CHALLENGES | |
✓ | EXTENDED CONTENT BEYOND TOURNAMENT MATERIAL | |
✓ | 4 MONTHS OF UNLIMITED 24/7 ACCESS - ANYWHERE, ANYTIME | |
✓ | ✓ | HINT SYSTEM FOR LEARNING OPPORTUNITIES WHEN STUCK |
✓ | ✓ | FOR INDIVIDUALS |
✓ | FOR TEAMS | |
✓ | PRIZES FOR TOP SCORERS | |
✓ | IN-PERSON NETWORKING OPPORTUNITIES | |
✓ | TRAVEL REQUIRED (FOR IN-PERSON TOURNAMENTS) | |
✓ | ✓ | PARTICIPATE AT HOME (LIVE ONLINE TOURNAMENTS & CONTINUOUS) |
6 | 12 | CPE CREDITS |
Product Specifications
NetWars Core Tournament
NetWars Core is an industry leading multi-disciplinary cyber range that covers a wide range of subject matter. It is the most comprehensive and diverse of the NetWars focus areas. NetWars Core is recommended for all infosec practitioners.
NetWars Core Version 9 Overview
SANS NetWars Core Version 9 is super accessible and broadly applicable. Students from SEC301: Introduction to Cyber Security, to SEC760: Advanced Exploit Development for Penetration Testers can get through challenges with hints (or not!) and earn points.
NetWars Core Version 9 Story
A group of young friends are facing terrible danger, possibly associates with the local Hackins National Laboratory. You can help! Help defend our heroes - find out who's behind all this and maybe even strike back.
NEW Topics in NetWars Core Tournament Version 9:
- Cyber threat intelligence
- Azure command line
- Azure cloud penetration testing
- Network protocol analysis
Example Topics in NetWars Core Tournament Version 9:
- Linux command line
- Windows command line
- Malware reverse engineering
- Firewall configuration
- Forensics
- Incident response
- OSINT
- Web application penetration testing
- API penetration testing
Computer Requirements:
- Browser-based
- Preference for Chromium-based web browser
- 8GB of RAM
NetWars Core Continuous
NetWars Core Continuous is an extension of Core Tournament, meant solely for individuals, and covers an even wider range of subject matter for deeper skills assessment and practice. It is for all individual infosec practitioners and offers the convenience of 4 months of extended access, anywhere in the world.
Extended topics in NetWars Core Continuous include:
- Powershell offense, defense, survival
- API Manipulation
- Hash extension exploitation & Cryptographic security controls
- Linux terminal
- check file contents with head, tail, cat, less, and wc
- check OS version with uname and lsb_release
- verify basics with hostname and whoami
- searching environment variables with env and grep
- verifying user data with /etc/passwd
- testing file access controls with su
- elevated permissions with sudo
- file analysis with strings
- running process analysis with ps
- stopping processes with kill
- command history analysis with .bash_history and grep
- inspecting insecure password storage with recursive grep
- comparing files with diff
- modifying file permissions with chmod
- file integrity checking with md5sum
- Base64 encoding/decoding with base64
- output manipulation with sed, awk, rot13, sort, uniq, tr, and cut
- binary analysis with xxd
- task scheduling with cron
- PowerShell terminal
- filesystem analysis
- environment variable analysis
- running process analysis
- stopping processes
- Base64 encoding/decoding
- searching for files with given name/contents
- file integrity checking
- command history analysis
- compressed file manipulation
- loop operations
- conditional operations
- web requests
- alternate data streams (ADS)
- Packet capture analysis
- analysis with Wireshark
- file extraction from stream with Wireshark
- basic traffic filtering with Wireshark/Tshark display filters
- advanced traffic filtering with Wireshark/Tshark display filters
- malicious traffic identification
- HTTP(S) analysis
- identifying vulnerabilities and flaws with Wireshark and Tshark
- server-side JavaScript Injection (SSJS)
- SQL Injection (SQLi)
- Remote File Inclusion (RFI)
- Insecure File Upload
- Command Injection
- HTTP requests with cURL
- deobfuscating JavaScript with web browser developer tools
- manipulating JavaScript objects with web browser developer tools
- HTTP2 analysis
- vulnerability scanning with Nikto and wpscan
- cookie manipulation
- Network Analysis
- raw connections with netcat
- network connection status with netstat
- port and version scanning with Nmap
- secure file transmission with scp
- dynamic proxies
- malicious traffic matching with Snort
- packet capture with Tcpdump
- filtering traffic with Berkeley Packet Filters (BPF)
- DNS querying with dig, nslookup, and nsupdate
- network defense with iptables
- packet dissection and crafting with Scapy
- application fuzzing with boofuzz
- SMB connections with smbclient
- Penetration testing (system, network, and web application)
- password cracking with John the Ripper
- password guessing with THC Hydra
- password guessing with wfuzz
- exploit research with online, open databases
- exploitation with Metasploit
- SQL database exploitation manually and with SQLMap
- social engineering with the Social Engineering Toolkit (SET)
- cookie stealing with cross-site scripting (XSS)
- malware generation with msfvenom
- LDAP injection
- API manipulation
- deserialization attacks
- manual Windows vulnerability enumeration and exploitation
- privilege escalation
- Scripting
- Python scripting
- Perl scripting
- Forensics
- file forensics with Volatility
- file extraction with Scalpel
- Linux executable analysis with GDB
- Data analysis
- database analysis with SQLite
- regular expressions (regex)
- metadata analysis with exiftool
- PDF analysis with pdftotext
- JSON manipulation with jq
- QR code generation
- Cryptography
- securing data with gpg
- hash extension exploitation
Computer Requirements:
Processor
64-bit, x86, 2.0 GHz+Memory
16GB*HD
40GB+ FreeOperating System
Windows 10 or later, Mac OS 10.15 or later, LinuxSoftware for Range
VMware Virtualization* 8GB is possible with reduced performance
NetWars Cyber Defense Tournament
NetWars Cyber Defense is specifically focused on cyber defense and threat detection; prevent, defend, and analyze increasingly more complex, real-world attack scenarios against your enterprise, from simplistic, brute-force attacks to ransomware campaigns.
Professionals who should consider taking NetWars Cyber Defense include experienced Security Administrators, Enterprise Defenders, Architects, Network Engineers, Incident Responders, Security Operations Specialists, Security Analysts, and Builders and Breakers.
Example topics in NetWars Cyber Defense Tournament include:
- Cyber Defense
- Threat Hunting
- Log Analysis
- Packet Analysis
- Cryptography
- Windows Administration
- Linux Administration
- Network Security Monitoring
- Continuous Security Monitoring
- Steganography
Computer Requirements:
Processor
64-bit, x86, 2.0 GHz+Memory
16GB*HD
40GB+ FreeOperating System
Windows 10 or later, Mac OS 10.15 or later, LinuxSoftware for Range
VMware Virtualization* 8GB is possible with reduced performance
NetWars DFIR Tournament & Continuous
NetWars DFIR is specifically focused on digital forensics, incident response, threat hunting, and malware analysis, that is tool-agnostic, from low level artifacts to high level behavioral observations.
Professionals who should consider taking DFIR NetWars include experienced Digital Forensic Analysts, Forensic Examiners, Media Exploitation Examiners, Malware Analysts, Incident Responders, Threat Hunters, Security Operations Center (SOC) Analysts, Law Enforcement Officers, Federal Agents, Detectives, and Cyber Crime Investigators.
Example topics in NetWars DFIR Tournament include:
- Digital Forensics
- Incident Response
- Threat Hunting
- Malware Analysis
- SIFT Workstation (sans.org/tools/sift-workstation)
- Smartphone Forensics
- Windows Forensics
- MacOS and iOS Forensics
- Network Forensics
- Media Exploitation
- Artifact Analysis
- Rapid Triage
- Database Analysis
- Log analysis
- Malicious attacks
- Network traffic analysis
- Reverse engineering and debugging
- Intrusion detection
Computer Requirements:
Processor
64-bit, x86, 2.0 GHz+Memory
16GB*HD
200GB+ Free. Approximately 50GB download of evidence files and virtual machines.Interface
USB 3.0 | Type-A or dongle with Type-AOperating System
Windows 10 or later, Mac OS 10.15 or later, LinuxSoftware for Range
VMware Virtualization. Participants are expected to either provide their own forensics tools, or use the local VMware VM tools that we provide.* 8GB is possible with reduced performance.
Netwars ICS Tournament
NetWars ICS is specifically focused on industrial control systems and operational technology. It employs a literal cookie factory to unite the ICS/OT factions over the one true sweet treat; nom nom cookies. End goal: get the factory machinery working correctly so you and your peers can be rewarded with fresh baked cookies. ICS NetWars will bring players onto the factory floor and expose them to physical equipment and manufacturing components as they work through the NetWars scenario.
Professionals who should consider taking ICS NetWars include experienced Process Control Engineers, ICS/OT cybersecurity practitioners working in operational facilities, and IT cybersecurity professionals supporting ICS environments.
Example topics in NetWars ICS Tournament include:
- Blue Team (Defender) actions
- Asset discovery and infrastructure mapping
- Identifying adversary actions
- log and file analysis
- Endpoint forensics
- ICS-specific malware detection
- Engineering application use
- Process restoration
Computer Requirements:
Processor
64-bit, x86, 2.0 GHz+Memory
16GB*HD
40GB+ FreeOperating System
Windows 10 or later, Mac OS 10.15 or later, LinuxSoftware for Range
VMware Virtualization* 8GB is possible with reduced performance
Netwars GRID Tournament
NetWars GRID is similar to NetWars ICS in that it is focused on industrial control systems and operational technology. However, the NetWars GRID scenario is designed around the complex nature of distributed wide-area control systems found in critical infrastructure sectors like electric system operations. Utilizing a variety of real-world technologies found in electrical generation and distribution systems, the challenges are themed to the power system scenario, though the technology, protocols, architectures, and lessons learned are applicable across numerous critical infrastructure sectors beyond the electric sector.
Professionals who should consider taking GRID NetWars include experienced IT and OT cybersecurity professionals supporting SCADA communications and control, field technicians, instrumentation and control, ICS field or plant control systems, and control center OT support teams.
Example topics in NetWars GRID Tournament include:
- Adversary actions
- ICS Stage 1 and Stage 2 kill chain
- Spear phishing
- Command and control
- Credential theft
- Lateral and vertical movement
- Security configuration modification
- Process manipulation
- Situational awareness impacts
- Reliability effects
- System integrity impacts
- Blue Team (Defender) actions and Red Team (adversary) actions*
*Variations of Netwars Grid exists
Computer Requirements:
Processor
64-bit, x86, 2.0 GHz+Memory
16GB*HD
40GB+ FreeOperating System
Windows 10 or later, Mac OS 10.15 or later, LinuxSoftware for Range
VMware Virtualization* 8GB is possible with reduced performance
NetWars Healthcare
NetWars Healthcare is based on the technologies and systems found in the medical field. It still features the rich storylines, hints, TAs and game servers as other NetWars ranges, but is browser-based for easier access and deployment.
Example topics in NetWars Healthcare include:
- Telemedicine and web app security
- EMR and incident analysis
- Medical device IoT security
- Ransomware analysis and decryption
- Hospital incident investigation with Windows domain event log analysis
Computer Requirements:
Internet Access and Chrome, Firefox, Safari, or Edge browsers.NetWars | Federal Government
All varieties of NetWars are PCTE compatible.
Persistent Cyber Training Environment (PCTE) is a training platform that supports Joint Cyberspace Operations Forces by providing individual sustainment training, team certification, mission rehearsal, and the foundation for collective training exercises. It leverages existing connectivity to facilitate the sharing of resources, and provides additional cyber “maneuver space.” PCTE enables realistic training with variable conditions to increase readiness and lethality of our Cyberspace Operations Forces, while standardizing, simplifying, and automating the training management process.
PCTE supports the United States Cyber Command (USCYBERCOM) by enabling a critical need for the DoD and Joint Cyberspace Operations Forces to train at the individual, team, and force level. PCTE is one of the five elements of the Joint Cyber Warfighting Architecture (JCWA), provides a comprehensive, integrated cyberspace architecture to achieve and sustain the insight, agility, and lethality necessary for maintaining a competitive advantage against near-peer adversaries. PCTE will integrate and be inter-operable with the other JCWA elements to enable teams to train and rehearse using the available JCWA operational tools and capabilities.
Bootup CTF is a capture-the-flag style cyber range consisting of over 125 multi-disciplinary cybersecurity challenges. It can be played solo or as a team. Bootup runs virtually online for 24-72 hours. Players can log in to participate or log out to take breaks at any time, multiple times, during the open session. Bootup CTF also features an automated hint system to help participants with supporting material and content related to the questions.
- Question and answer format
- Play on your time
- Modular
- Browser based
- A wide variety of topics
Bootup CTF is for individuals and teams of all levels. While the content is primarily beginner to intermediate, it provides an easy and convenient way to challenge yourself on the myriad of topics every cybersecurity professional faces daily. Because of the modular nature of Bootup CTF, you can engage and learn at your own pace, in contrast to the brain-crunching environment of other learning formats. And for the cherry on top, every Bootup CTF features prizes for the top scorers of the game.
Computer Requirements:
Internet Access and Chrome, Firefox, Safari, or Edge browsers.
Upcoming NetWars Tournaments
| Date | Location | NetWars Tournament |
|---|---|---|
| Apr 11-12 | London | GB | DFIR NetWars |
| Apr 18-19 | Amsterdam | NL | Cyber Defense NetWars |
| Apr 25-26 | Austin, TX | US | Core NetWars |
| Apr 25-26 | Oslo | NO | Core NetWars |
| May 12-13 | San Diego, CA | US | Core NetWars Cyber Defense NetWars |
| May 15-16 | Munich | DE | Grid NetWars |
| May 23-24 May 30-31 | Amsterdam | NL | DFIR NetWars Core NetWars |
| Jun 6-7 | Munich | DE | Cyber Defense NetWars |
| Jun 13-14 | Paris | FR | DFIR NetWars |
| Jun 22-23 | Orlando, FL | US | ICS NetWars |
| Jun 27-28 | San Antonio, TX | US | Core NetWars |
| Jul 18-19 | Washington, DC | US | Core NetWars Cyber Defense NetWars |
| Aug 27-28 | Salt Lake City, UT | US | DFIR NetWars |
| Sep 7-8 | Las Vegas, NV | US | Grid NetWars Core NetWars |
| Sep 19-20 | Baltimore, MD | US | Core NetWars |
| Oct 31 - Nov 1 | Orlando, FL | US | Core NetWars |
| Dec 16-17 | Washington, DC | US | Core NetWars |